Can you really take advantage of the best booter if you happen to end up beneath the attack of the DDoS ? The following are the first things you will probably have to accomplish:
•The ISP and information centre should be informed immediately
•The ransom transaction has to be an option that is a transaction leading towards the ransom demands that happen to be escalating
•Police force companies really need to be notified
•There has to be checking of your system visitors
•Reach on the defense strategies of DDoS
How can you really mitigate botnet attacks?
•Firewalls should be set up on the host
•Spots of protection must be up to date
•Antivirus computer software must be operate on routine
•Solutions logs need to be observed regularly
•E-mail servers which are not known will not be allowed to deliver SMTP visitors
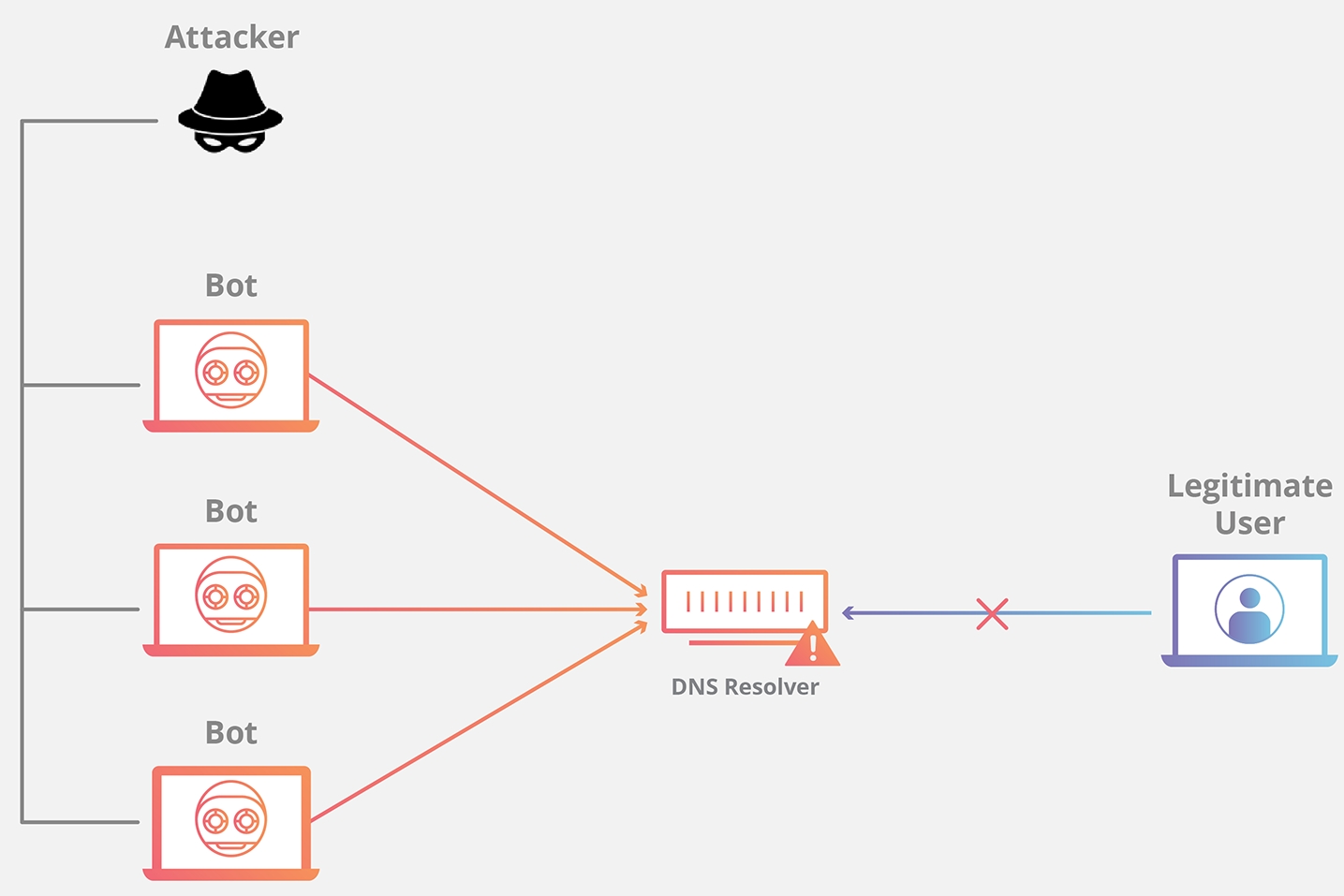
Why it really is that booter services are hard to track?
The individual that buys the felony professional services uses a website frontend for settlement and instructions that are based on the invasion. Usually, there is absolutely no relationship which is unidentifiable on the supported starting the true assault. Therefore, criminals who have an intent can often be difficult to be established. Using the path of repayment may be a great way of having the capability to path the felony organizations.
Do you know the denials of assistance assaults categories?
Application coating episodes do opt for the web programs, and mostly utilize the most sophistication available. The assaults make use of level 7 protocol some weakness piles by getting to first establish a experience of the marked, then exhausting the resources web server by having to monopolize transactions and processes. They can be quite difficult in figuring out and mitigating. A great example is the HTTP deluge attack.
Episodes that happen to be protocol based that concentrates on needing to exploit the weeknesses in the covering 3 and coating 4 of the stack of process. These kinds of strikes are known to take in all the potential of handling from the target or some other solutions that happen to be essential such as a firewall, which in turn results in the disruption of support, ping of passing away and syn deluge are case in point of the identical.